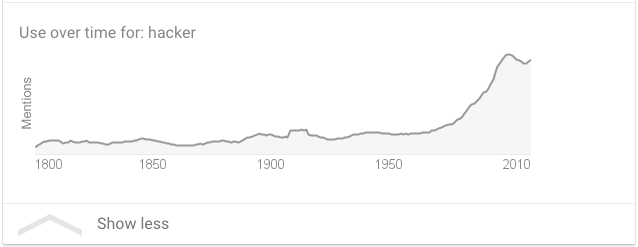National Cyber Security Awareness Month: What is Cybersecurity?
Welcome to part one of a five-part series in honor of National Cyber Security Awareness Month. For the month of October 2018, I’ll be featuring one article per week going over four main topics; online safety for the whole family, cybercrime and cybercriminals, managing sensitive data on computers and mobile devices, and managing privacy both online and in the real world. Any good series on cyber security awareness should start off with a definition of what exactly cyber security is. To that end, forgive me for stepping back a bit to launch first into a definition of family and family safety before taking things into the cyber realm.
A family can be one person, that is, just yourself, two people in many varying combinations, or more people, who live together or share a familial bond either through blood or sheer dedication to one another. In Puerto Rico, where I lived for over a decade before coming back to Upstate New York, the law there defines a family as those who mutually help one another, share meals under the same roof together, and whom generally depend on each other for emotional and financial support. This is probably my favorite definition of family to date. It also expands from a more blood-relative tradition into a more communal setting. How does this, perhaps, ampler definition of family tie in to the idea of family safety in this day and age?
I decided to ask around about some basic family safety rules that our readers might be able to identify with or may have even had in their homes growing up. The first rule I came across was to only let mommy or daddy answer the door. This coincided with a similar rule, don’t let strangers in the house, or if there’s a peep hole in the door, maybe even, don’t open the door for strangers. Rule number two seemed obvious, don’t hide a key to the front door under the door mat, or in another obvious place. Finally, a third rule that kept coming up, especially in urban settings is, keep the doors locked even when you’re at home. I’ll add that all three of these rules were noticeably absent from my upbringing, being from a very small rural community where everyone left their doors unlocked and would generally welcome any visitor into their homes. Times have changed, and so has technology’s role in our lives.
All these in-real-life ideas center around three concepts that should be familiar to any student of cybersecurity or information technology; access control or authorization, authentication, and accounting. Cybersecurity is defined by Google’s Dictionary as “the state of being protected against the criminal or unauthorized use of electronic data, or the measures taken to achieve this.” The tripe-A’s of authorization, authentication, and accounting fall under the latter portion of the definition as “measures taken to achieve this.”
Graph 1 – Usage of the term “cybersecurity” over time, by Google. (Retrieved 10/3/2018)
Cybersecurity, as seen in the graph that Google provided when researching the definition, hasn’t been around for very long, and for good reason. Electronic information systems, not unlike telephones and television, have only existed for a relatively short amount of time in human history. Until computers came to be in the mid-1900’s, the only ‘security’ researchers and developers were concerned about was preventing physical access to the machines and systems in development. Even then, the archaic methods used to input data and/or read the results kept these now ancient information systems effectively secure through a widespread lack of understanding as to how they even operated.
The visible spike around the 1970’s in the graph above was when computers started to talk to each other via the public switched telephone network, or PSTN. This meant that a tech savvy individual of the time could dial a phone number, even random numbers sometimes, and at the other end a computer might have been the only thing answering their call. The more businesses and universities adopted computerized technology to process their daily, monthly, and yearly workloads, the more likely a would-be hacker was able to dial a phone number and gain access to the back-ends of the systems. Searching Google for the definition of the word hacker will show a steep curve upwards around the same time as the graph above starts to clock the mentions of cybersecurity. Just keep in mind, before computers came around, the world knew hacker to mean someone or something that chopped or cut things up.
Graph 2 – Usage of the term “hacker” over time, by Google. (Retrieved 10/3/2018)
Those first, now seemingly ancient, systems relied on the principle of the unknown to keep themselves safe; ‘if we don’t give out the phone number, no one will have access.’ That proved to be a mistake that has kept up into the modern day. Luckily, cybersecurity interests started to introduce the idea of authorization and authentication into the mix. If one would keep their front door locked, why not keep the back door locked as well? Businesses were more than used to keeping their assets under lock and key. Universities, governments, and research and development firms knew to keep their assets away from prying eyes and hands. So, why not secure this new category of electronic assets in a similar fashion? This was accomplished by both reducing public access and issuing usernames and password to users. So then, even if someone were to guess the phone number to a centralized computing system’s modem, they would also need a set of digital credentials to truly gain access.
Fast forward almost thirty years, and computers emerged from the basements of companies and schools to take up residence in people’s homes. With hardly a thought to the idea of cybersecurity, families around the country eagerly inserted AOL and Prodigy branded compact discs into their personal computers’ CD-ROM drives and connected their PCs to phone lines for the first time. The Internet in the 90’s tended to arrive hand-in-hand with the home PC. One saving grace at the time was that a home PC, though connected to the phone line, generally wouldn’t pick up if someone called. So why would a family have to worry about cybersecurity? The answer remains simple yet elusive to many homes; by connecting to the Internet and accessing online content, computers download files. For a shared home PC this is akin to inviting strangers into the home, only in the form of webpages, programs, or media files needed to access and display online content.
As computing power and transmission speeds increased, so did the connectedness of the home PC. Families started performing more day-to-day functions over the Internet, such as shopping, communicating with friends and family, and banking. Each website or activity would come with its own, hopefully unique, username and password. Early users of the Internet were warned to never give out personal information to anyone; no names, definitely not their home address or phone number, and even worse would be divulging the username and password to one’s bank account. People understood the importance of not giving out their credentials, just like they understood not giving out copies of their house keys to random strangers.
So again, what changed? If people kept their username and passwords a secret, how were they still vulnerable? The problem was, and still is, that hackers know that people were lazy, both on the administration side of accounts and the user side of accounts. Usernames that were assigned were often made up of knowable combinations of the users’ first initials plus their last names. In high school, my username was simply “cbovee” when I graduated in 1999. Almost twenty years later, the user naming scheme in place at the SUNY Polytechnic (as any student here can tell you) isn’t substantially different. This makes guessing the first part of a key combination as easy as meeting someone who worked or studied at a given location. The user laziness, however, comes in to play when a user applies an easy to guess password to their account.
In all of this, the Internet forced upon its users a new way to address one another in the similar fashion to knowing each other’s home address; electronic mail, or e-mail, as it’s called today across multiple languages. In the beginning, e-mail accounts were precious. They only given by your Internet Service Provider, based on your dial-up account’s username and using the same account’s password. For a great majority of the average users in the 1990’s, the domain name of a given e-mail address was very likely to end in aol.com, compuserve.com, prodigy.com, or earthlink.com. Each of these domains represented in their day hundreds of thousands of paying dial-up users. E-mail had limitations; the size of a user’s inbox, the size of individual e-mails, and to make it all nice and cozy, most families had only one email address.
The activities I mentioned earlier; shopping, communicating with friends and family, and banking; all required having access to a working e-mail address, and still do today. Shopping and banking online also require access to the receipt of postal mail, not to mention money and a job to earn it with. What else has changed? To have Internet access, people used to have to own or rent a home, possess a computer, a phone or cable line and an account to connect with. In 2018, all people need is a smart-phone and some form of subscription-based service that enables it to connect to the Internet. Sadly, not much more than a phone and an Internet connection are all that’s required to steal someone’s online identity and many of the associated accounts.
Cybersecurity is more than keeping e-mail accounts secure and coming up with unique passwords like $dgtr5r^DF23. Modern cybersecurity concerns at the home level also include parents monitoring their children’s online accounts, which necessarily includes knowing their kids’ passwords and login information. Cybersecurity for the family is also setting the in-home wi-fi router to broadcast a generic name and use a long and complex password, instead of ‘Jones Family Wifi’ and ‘password123456’. With advancing technology in smart-homes, smart-devices, and networked home entertainment; keeping individual components up to date can mean the difference between NetFlix and chill, or those devices taken over by hackers and used en masse to carry out online attacks.